
Getting ready for another server migration and unsure of what steps you need to take?
If your website or application is changing or growing over the months and years, then it is nearly inevitable that at some point you’ll need to change servers.
When the time comes, be prepared with the following guide on preparing your server and team for migration day and beyond.

What is a Server Migration?
A server migration is the term used to describe copying or moving critical data from one server to another, as well as configuring that target server to replace the first. Server migrations in the context of web hosting might revolve around setting up web server and database software, copying over websites and their configurations, and changing DNS to direct visitors to that new server.
Why Should I Consider a Server Migration?
Server migrations may need to happen for a number of reasons. Organizations may migrate to:
- Take advantage of new technology or better service, or to ensure that the operating system (OS) and the hardware beneath it stay up-to-date with current technology.
- Move to the cloud for increased flexibility or scalability.
- To economize and consolidate hosting and reduce CapEx.
- Replace aging infrastructure at the end of its lifecycle.
- To expand and distribute hosting to help reduce load at a single point and achieve high availability.
Migrations should be handled with utmost care. You could sink hours of time, effort, and money into a migration only to find yourself onto the wrong server solution, or worse, with downtime and profit loss. It takes considerable planning and forethought to migrate your data onto an optimized server that is right for you. After all, on-average downtime can cost an enterprise $686,000 an hour, so your organization’s success absolutely depends on a successful migration.
How Do I Plan for a Server Migration?
Despite the fact that server migrations are quite common, even the most experienced IT professionals experience nervousness when it’s time to actually make a move. With so many moving parts and required precision, it is very easy – and very common – for migrations to be approached with at least a little anxiety.
Alleviate tension by planning ahead for the migration.
It is important to think about data migrations early, because planning ahead is particularly critical for ensuring smooth, fast migrations that deliver the intended benefits without causing a lot of headaches along the way.
While a checklist is important to have, moving to a new environment is a complex procedure, and even knowing what belongs on the migration checklist requires careful consideration.
Organizations that do not leave a long enough lead time for their migration project often find that they experience business disruptions or unexpected costs, even if they do everything else right.”
A clean data migration plan requires extensive system exploration and preparation by the company’s IT personnel, but even after the most diligent preparation, surprises are possible. Because several of the steps require the attention of IT teams or may consume a large amount of bandwidth, those steps should be carefully scheduled.
A complete and accurate picture of your existing infrastructure, including all data, hardware, software, and network components is necessary for a successful data migration. A full documentation of your infrastructure is used to properly architect your new environment before the migration even begins, and enables you to avoid missing anything when the migration is performed.
This resource also informs the rest of the planning process. Performing a thorough discovery can also have the side benefit of uncovering potential future problems, like forgotten web applications running an unsupported scripting language.
Preparation takes many forms beyond the initial exploration phase, including scheduling, communicating with staff, and technical measures such as updating the LAMP stack if necessary, along with code and plugins.

5 Step Server Migration Plan
- Preparing Your New Server
- Assess Data Fidelity
- Data Transfer
- Testing (QA/QC)
- Changing DNS and “Going Live”
As we mentioned, a complete and successful migration is made up of a number of steps that can be performed sequentially. Those steps tend to fall into one of five primary categories that make up the overarching process of a migration.
Understanding how these broader steps fit together, and what is included in each, is critical to developing your exact migration strategy in the future.
1. Preparing Your New Server
In the simplest terms, think of a server migration as moving from one home to another. If you want to bring all of your possessions with you, then your new home needs to have enough space for all of your furniture, right? And, if you are used to having, say, a double sink vanity in your bathroom, you may want the same features in your new home.
Migrating to a new server is much the same. All of the data associated with your website and applications needs to fit properly and in the right place on your new server. As a result, it is critical that your new server be properly sized and prepared for any incoming data and digital assets. Additionally, make sure that services and packages that your sites depend on are installed and available in the new environment.
Key Questions to Consider During Server Preparation
- What is your organization’s planned growth over the next five years, and what infrastructure changes will this require?
- Are all the right parties involved or informed of the planned migration? Think about site editors, administrators, developers, visitors or end users, and your hosting provider(s).
TIP: Build in approximately 20% extra storage space when migrating. During the migration, you’ll need a little extra room to unpack and install the data that’s being migrated, and you will want some room to grow as well.
2. Assess Data Fidelity
The process of making sure all data is accounted for before the migration, and properly installed after, is of critical importance. Losing even a tiny fraction of your data in transition, such as one CSS file or one connection string, can impact the performance of your entire site or application.
We recommend spending some time prior to the migration taking note of what parts of your site are critical, and what parts interact with or engage with other services.
For example, plugins and themes that affect multiple pages should be checked both before and after migration to ensure identical functionality.
Key Questions to Consider During Data Fidelity
- What is the quality of your data in your old server? Are there a lot of static files, or dynamic databases?
- Do you have a data governance plan in place to ensure measurement, tracking, and better decision making during the migration process?
3. Data Transfer
Once you have prepared your new server and properly secured all data to be ready for the migration, it’s time to finally make the copy.
Data transfer is typically the most time-consuming part of migration. The bandwidth available between your old server and the new server (or between your old hosting provider and your new hosting provider) essentially serves as the conduit for the migration. The more bandwidth you have, the faster the data can be migrated.
Key Questions to Consider During Data Transfer
- Are all parties on the same page regarding when data transfer will take place?
- Is there a clear POC at your old hosting provider and at your new hosting provider?
- Are there any major initiatives or high-traffic events planned during or around the planned migration timelines?
TIP: Let anyone with access to the site know when the migration is going to happen and how long it is expected to take. Putting a “freeze” on any websites or applications will better ensure that no new content or data is lost during the migration.
4. Testing (QA/QC)
Once you’ve actually migrated the data to your new infrastructure, it’s time for testing.
Checking for full functionality and complete data transfer may be time consuming and cumbersome, but that is time well spent to prevent discovering an issue at a much later date. Because it is usually the part of the process where surprises are most likely, it can also vary significantly in how long it can take. Organizations often find that leaving an adequate amount of time to fully and properly complete the testing process is much easier if planned well in advance.
Conducting rigorous testing is how organizations identify unanticipated issues, evaluate the effectiveness of their strategies for dealing with known issues, and confirm the many details about how the process and running in the new environment will work.
Finally, document HOW you will perform testing post-migration to ensure quality assurance and quality control.
Key Questions to Consider During Testing
- Have you verified appropriate request responses for APIs between applications and servers?
- In multi-server setups, are public and private traffic moving along the appropriate networks?
- Are your site(s) or application(s) performing as expected?
TIP: Reference your previous site and server during the testing process to see if anything looks off or incomplete. So long as the prior server was functional, it can provide a good road map for what your website should look like in its early life on the new server. Sometimes, existing site issues can be uncovered during migrations!
5. Changing DNS and “Going Live”
Now that you’ve migrated all of your data, applications, and websites to your new server and performed sufficient testing, it’s time to switch your DNS so traffic goes from the old server to the new infrastructure.
Switching DNS is actually a relatively simple process in most cases. We suggest your DNS switch take place during a time of low traffic and low usage. The middle of the night or the weekend can be the best time for the change.
Key Questions to Consider When Switching DNS
- Have you double checked there are no business-critical events in the next 72 hours following “go live?”
- Are all parties clear on their duties for the “go live” event?
- Do you have a backup, reversion, or correction plan in case something goes wrong?
Keep the Old Server Active as Short-Term Protection
Curious what to do with your previous server now that it is not in use? Our recommendation is to leave the old server active for at least a week or two as a point of reference and fallback option in the event an unknown problem rears its head.
Leaving your old server running for a transition period offers excellent protection against the most unforeseen issues.
What Should You Avoid During Server Migrations?
Avoid the following during server migrations:
- Avoid scheduling a move immediately before a critical period for your business, such as Black Friday for an online retailer, to prevent a situation in which a minor problem needs to be fixed in an unrealistic time frame and becomes a major disruption.
- Migrations should generally be performed during off-hours or times when a minimal amount of business is expected. This limits the chances of a disruption, but also gives the IT team an opportunity to focus solely on the migration, and prevents the legacy environment from being overwhelmed or the network from becoming saturated.
- Avoid starting a migration until the exploration period is complete. An incomplete exploration is one of the main sources of preventable problems in migration projects of all kinds.
- Notify staff outside of the migration team about the migration, including migration timelines, the changes expected to occur, and responsibilities, if any, that may be included as part of the project. It may be necessary to create or make available documentation and have a window of time in which IT personnel can assist other staff or end users with any initial set-up.
How Can a Service Provider Help With Server Migrations?
Most service providers offer to help with migrations, addressing a significant pain point for their potential customers. However, not all hosts have the combination of customer migration skill and motivation to follow through in a way that actually makes the experience as smooth as possible.
The requirements for migrations are significantly different depending on what is being migrated, and the environments involved.
As we previously wrote about migrating data between cPanel servers, service compatibility is the real magic of migrations. The magic spells, in this case, are the configurations and combinations of versions which will work together.”
This can get quite complicated.
In the discovery and documentation portion of the process, your web hosts’ migration veterans can work with the organization’s IT administrators to make sure that all relevant information is identified from the beginning, so they know what to look for. They can also help estimate how long some of the steps will take, including the final move.
Important details about how a particular kind of environment runs, such as ensuring quorum is established in a server cluster, may be obvious to migration experts, but not so clear ahead of time to in-house IT staff in the midst of a major operation. Likewise, after helping organizations through many migrations, service providers can help IT teams anticipate some of the questions they are likely to be asked by staff.
The experience service providers gain from migrating customers is only part of the expertise organizations can benefit from when making a change.
Crafting a new environment to suit your business’ needs is challenging, even once you have completed a thorough discovery, and guidance from professionals who have detailed knowledge of all of the prospective new environment’s elements can be invaluable to making the right move. Likewise, the experience of experts in storage and networking, your operating system, and the particular systems you are migrating from and to can all be valuable resources during the data migration process.
A service provider with extensive experience assisting customers in different kinds of migrations can be an invaluable asset. From exploration and creating a project plan through testing and execution, there are numerous potentially expensive pitfalls that organizations can avoid with the right help.
A Better Understanding of Successful Server Migration Steps
Server migrations are simple to understand and yet often complex to execute.
Believe it or not, that’s a great thing!
The overarching concepts that make up a successful migration mean anyone can do them, and the details of each step, while often numerous, are not necessarily difficult. That said, one of the best things you can do to ensure a successful and complete server migration is to engage experts that know the path and can guide you on the journey.
Here at Liquid Web, our Most Helpful Humans in Hosting perform thousands of migrations every year, and understand what roadblocks to avoid and pitfalls to navigate.
perform thousands of migrations every year, and understand what roadblocks to avoid and pitfalls to navigate.
If you are considering migrating to a new server, get in touch now. We would be happy to discuss with you what goes into a successful server migration, and help architect the right infrastructure for your needs.
Migrating to a new server is a big decision, and a process best undertaken with a trusted partner by your side.
Struggling With Downtime From Your Current Host? Get Your Complete Migration Checklist.

The post A Complete Guide to Server Migration appeared first on Liquid Web.










![[Production Tracking Screen]](https://www.greytrix.com/blogs/sagex3/wp-content/uploads/2020/09/PT-1024x537.jpg)
![[Quality Control Screen – Q Status]](https://www.greytrix.com/blogs/sagex3/wp-content/uploads/2020/09/Q-Status-1024x539.jpg)
![[WO Close screen – Error Message]](https://www.greytrix.com/blogs/sagex3/wp-content/uploads/2020/09/Error-Message-1024x606.jpg)
![[Quality Control Screen – A Status]](https://www.greytrix.com/blogs/sagex3/wp-content/uploads/2020/09/A-Status-1024x545.jpg)
![[WO Status - Closed]](https://www.greytrix.com/blogs/sagex3/wp-content/uploads/2020/09/Closed-1024x613.jpg)
 integrations include
integrations include 

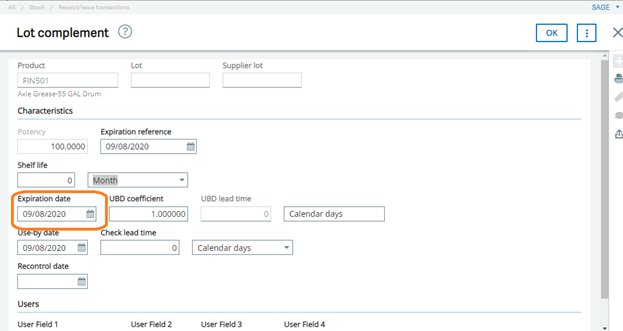
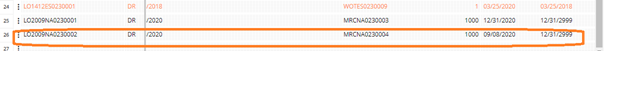
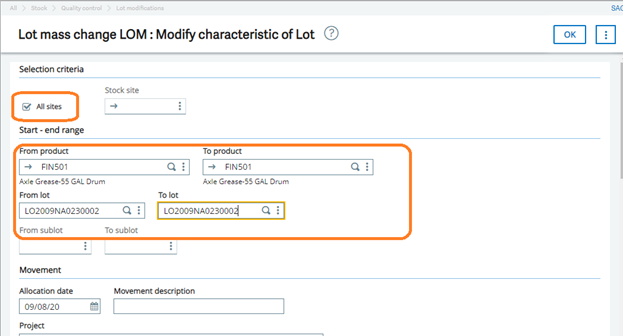
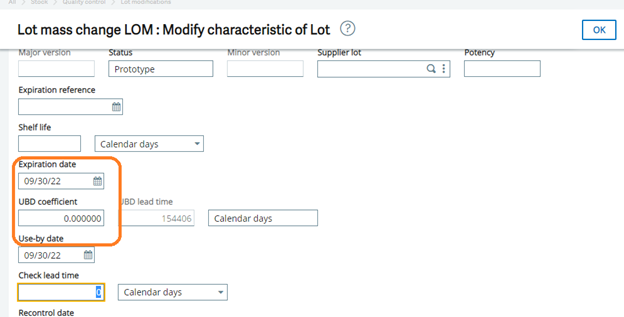


![[Manual Remittance Entry]](https://www.greytrix.com/blogs/sagex3/wp-content/uploads/2020/08/Manual-Remittance-.jpg)